"As Benjamin Franklin once said, ‘An ounce of prevention is worth a pound of cure.’" When it comes to cybersecurity, federal agencies have long focused on reacting to threats rather than preventing them. But in an era of rising cyberattacks, evolving threats, and complex IT environments, reactive security isn’t enough. Agencies must adopt a Start-Left approach—embedding security from the very beginning of the development lifecycle rather than bolting it on at the end.
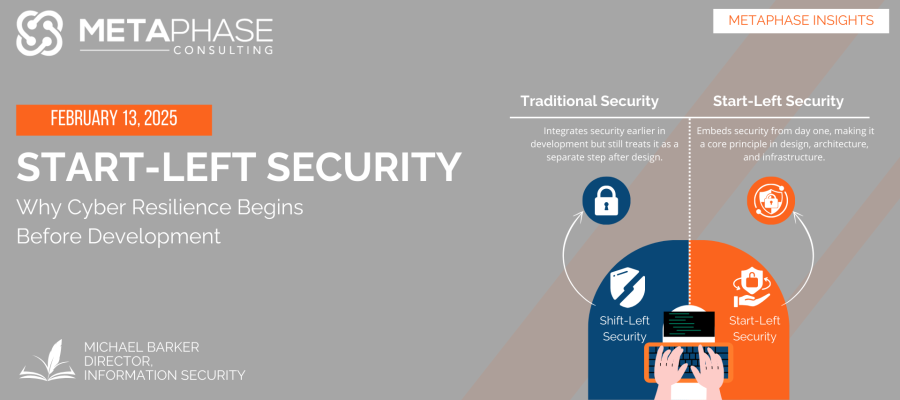
For years, federal IT teams have worked under a shift-left security model, integrating security earlier in the software development lifecycle. While shift-left is an improvement over traditional after-the-fact security assessments, it still assumes security is a separate step that follows design and development. Start-left security takes this further by making cybersecurity a foundational principle from day one—baked into design, architecture, and infrastructure decisions before a single line of code is written.
Consider Zero Trust architectures, which require continuous authentication and least-privilege access controls. A shift-left approach might introduce Zero Trust principles during testing and integration, but a start-left approach ensures identity management, encryption, and least-privilege access are fundamental design elements from the start. This dramatically reduces vulnerabilities and ensures security is not just a compliance requirement—but a core design feature.
Another example is federal cloud adoption. Agencies moving to the cloud often think about security only when they begin migrating applications, leading to costly retrofits and compliance gaps. A start-left strategy means designing for secure cloud architectures from the beginning, ensuring automated compliance checks, continuous monitoring, and security controls are embedded before deployment even starts.
The cost of not starting left is high. A study by IBM found that the average cost of a data breach in 2023 was $4.45 million—and in government, these breaches can compromise national security, disrupt critical infrastructure, and erode public trust. The National Institute of Standards and Technology (NIST) has emphasized that embedding security early can cut remediation costs by up to 30%, making start-left not only a security best practice but also a cost-saving measure.
The shift to start-left requires more than just new tools—it requires a culture shift. Agencies must rethink procurement, ensuring vendors build security into their products rather than patching it on later. Development teams must be trained in secure coding from the outset, and governance frameworks must prioritize security as a mission-critical enabler, not a last-minute compliance checkbox.
Federal agencies are under constant cyber threat. The ones that adopt a Start-Left mindset—treating security as a design principle rather than an afterthought—will be the ones best positioned to defend, adapt, and thrive in the face of evolving cyber risks.
MetaPhase works at the intersection of business-to-IT partnerships—creating, deploying, and supporting practical solutions that serve as a force multiplier for government.

